RISKS MANAGED.
COMPLIANCE ACHIEVED.
Netspective Opsfolio captures your risks, catalogs your IT assets, and documents your ops teams’ work. Plus it gives you an API-accessible central repository for sharing risks, documentation, and assets across systems. Use it to help prevent, detect or recover from security breaches.PII & PHI Data Risk, Security & Compliance Dashboard
Why Opsfolio?
Protecting your network and data has never been easy, and it’s only getting harder:
- Security attacks are increasing and hackers are getting more brazen.
- Regulatory requirements are growing, making compliance a moving target.
- Penalties for breaches and non-compliance are getting stiffer.
- Business, technical, and data risk identification and remediation are now a necessity.
- Lack of well-designed and automated incident response processes for detecting security vulnerabilities and handling breaches.
It’s what you don’t know about your IT operations portfolio that causes dangerous surprises:
- Your IT servers, storage, apps, and other asset inventory may not be documented, complete, or accurate.
- Your institution’s change control processes and tools don’t notify you of compliance gaps or security vulnerabilities.
- You’re unable to collaborate and communicate security, training, and compliance tasks with your staff or colleagues.
- You don’t know who is responsible and accountable for your assets or who should be informed or consulted about your assets.
Getting security wrong damages your business and brand. Getting compliance wrong risks financial penalties. Maintaining both security and compliance is not easy but it’s simpler than you think. It begins with focusing on your risks, selecting the right tools, and working with a trusted partner.
What is Opsfolio?
- Platform
- Centralized assets respository
- Multi-stakeholder risks repository
- Continuous monitoring
- On-premise & cloud agents for log shipping APIs
- Change management
- Anomaly detection
- APIs and SDKs for systems integration
- Apps
- Technology risks catalog
- Multi-device dashboard
- Operational assets inventory
- Staff collaboration & communications
- Training tracking
- Vulnerability management
- Analytics & reporting
- Services
- IT audit & scoring
- Cyber risk assessment & scoring
- Cyber risk actuarial data acquisition & sharing
- Penetration testing
- Remediation consulting
- Custom consulting
Audit & Assessment Services
Our on-demand consulting and assessment services use Opsfolio to help you:
- Conduct an environment survey to establish an IT inventory and identify the security stature of each asset.
- Find HIPAA, FISMA, or FDA QSR compliance gaps in your IT assets, change control processes, and update compliance related training.
- Find and mitigate obvious security vulnerabilities in your network and across your infrastructure.
- Build security and compliance monitoring strategies that adapt to changing threats and regulatory requirements.
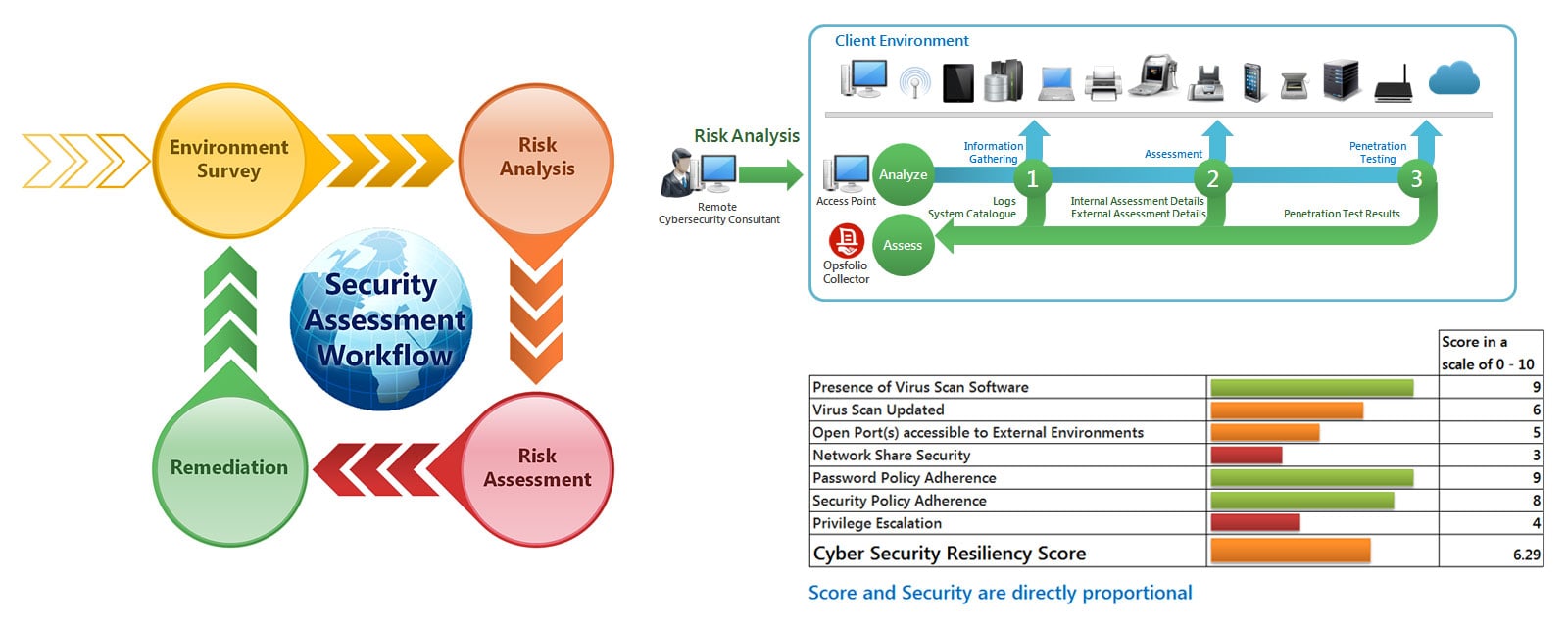
Netspective™ Opsfolio Audit for HIPAA helps you identify and address security and compliance issues relevant to Healthcare Covered Entities or Business Associates. Each audit includes these steps:
Gathering and analyzing all of your healthcare information management servers, apps, and other assets.
Customizing compliance policies for your care delivery organization or business associates.
Finding and classifying sensitive protected health information and preventing it from leaving your IT infrastructure.
Create easy-to-use management and technical reports that your own staff or partners can follow for remediation.

Netspective Opsfolio Audit for FISMA and FedRAMP helps identify the information controls that are required for the assets and procedures used in an organization’s unique operations. In each audit, our consultants:
Categorize each IT system and process and match them to the appropriate risk controls. Then, summarize the controls that match the IT assets and procedures.
Perform a gap analysis of FISMA requirements and organization policies, procedures and IT assets. Then summarize how well the current infrastructure satisfies FISMA requirements.
Perform risk impact assessment using NIST standards. This includes using new NIST (National Institute of Standards and Technology) standards for the New Authorization Process, Risk Management Framework (RMF) and Information Security Continuous Monitoring (ISCM) process.
Assess the compliance risk of the IT assets and FISMA procedures. Use risk assessment results to identity and justify funds for more effective security solutions

Netspective Opsfolio Audit for FDA provides the guidance and insight needed to meet FDA compliance requirements. In our FDA audits, our consultants:
Evaluate the classification of medical devices to identify appropriate regulations.
Identify predicate devices that are similar and already have a FDA 510(k) clearance. Then they judge whether these devices can be used in the 510(k) Premarket submission for the medical device.
Review FDA compliance, guidance, standards, testing and other specific requirements needed to claim substantial equivalence to predicate devices.
Build and maintain a compliance program that satisfies current requirements.
Easily manage assets and processes when standards change.

Netspective Opsfolio Audit for CUI helps you protect Unclassified Information in Non-federal Information Systems and Organizations and address compliance issues. In CUI audits, our consultants:
Perform CUI Compliance Audit based on NIST Framework for Improving Critical Infrastructure Cybersecurity
Access the compliance risks associated and provide guidance to support implementation of the NIST Framework for Improving Critical Infrastructure Cybersecurity.
Ensure CUI security requirements are met and provide a complete coverage report based on federal policies, standards, and guidance.

PCI compliance is a good way to increase customer confidence in your business and make sure that you’re not exposed to avoidable security breaches. PCI compliance audits:
Measure how well your POS system complies with APCI standards.
Identify potential data security vulnerabilities.
Help avoid compromising data privacy and security.
Identify specific problem areas
Preparing for successful PCI audits requires time, resources and experience. Netspective™ Opsfolio® Audit for PCI is an on-demand consulting service. We designed it to help corporate compliance officers and legal teams prepare for and engage in PCI audits. Opsfolio Audit for PCI services:
- Evaluate your data security infrastructure: This task includes IT network and systems as well as security procedures, policies and best practices.
- Perform a pre-audit risk assessment: We test your system, processes, documentation and practices—before the auditor arrives
- Increase security awareness in your company: This includes advice on training staff to improve security awareness. And, it gives all employees the knowledge and skills to meet current PCI standards and regulations.
- Prioritize security vulnerabilities: Rank any security vulnerabilities by the impact they have on your organization’s operations and business goals.
- Help manage audit preparations: We can manage the PCI audit process or act as a consultant, giving advice on how to improve PCI compliance.
The PCI audit process is complex and time-consuming. But correcting audit deficiencies will put an even bigger strain on your schedule and budget. To make sure you’re ready for a PCI audit, we assess your data security with:
Data discovery and analysis: We review your organization’s data security processes and practices to measure your level of PCI compliance.
Gap analysis: We compare existing processes and practices with those required for PCI compliance.
Risk assessment and testing: We identify vulnerabilities of with PCI-specific vulnerability scanning of internal and external networks, penetration testing, security assessments and automatic incident reporting.
Remediation: We provide expert advice, staff training and actual fixes to correct the vulnerabilities we find during testing.
Continuous monitoring: We watch your data security system continuously for IT, process and training shortcomings that need improvement.
Computer-controlled medical devices such as smart infusion pumps and alarm notification systems are increasingly available. More and more of these devices—which often configure themselves and identify and resolve problems automatically—are migrating to centralized enterprise networks.
These innovations make healthcare operations more capable and efficient. But, they also add multiple points of failure. These entry points of trouble often reduce patient safety and clinical data security.
Managing medical IT systems and complying with related regulations and standards take more time and effort than ever. Usually, that means:
Checking the effect of adding medical devices to your current IT infrastructure.
Having to check possible changes in medical device behavior every time you change the design of your network,
Having to check whether your medical IT device or system is in compliance every time the rules change.
If you fail to check changes diligently, patient safety or IT system security might be at risk.
Netspective® Opsfolio™ Audit for IEC 80001 is an on-demand consulting service. It’s designed to help healthcare providers, medical IT developers and medical device manufacturers identify and reduce data, patient and technology risk in their operations.
The IEC 80001 audit service helps:
Hospitals, clinics and medical practices connect medical devices to IT networks to achieve desired interoperability without compromising patient safety and data security.
Medical providers identify and reduce risks to patient safety and data privacy and security.
Medical IT developers and device manufacturers stay informed of the latest safety regulations.
The risk assessment service focuses on:
Risk management practices for IT networks that include medical devices.A practical, how-to approach to medical IT risk management.
Medical device safety based on risk analysis, evaluation and control.
Use Opsfolio Audit for IEC 80001 whenever you set up or make changes to your medical IT network. The service:
Monitors your medical IT network, its connection points and current configuration against compliance requirements.
Analyzes risks to patient safety or data security by gathering information, assessing security status and performing penetration tests.
Gathers, summarizes and assesses information and creates detailed reports of the risk assessment tasks performed and vulnerabilities identified.
Suggests ways to reduce system- and device-related safety and security risks.
Collaborate

Get a real-time snapshot of your organization’s assets and operations portfolio.
Netspective Opsfolio serves as a communications vehicle and notifications hub to facilitate communication of events at the asset level.
Understand network flows and make changes to the infrastructure easily and smoothly. Document lessons learned.
Opsfolio helps network administrators to quickly and effectively visualize infrastructure network flows. With Opsfolio, they can easily find out the vulnerability points and remediate it. Should any threats occur, our consultants can easily evaluate the severity by understanding how many assets were affected and the severity of each event.


Manage the compliance requirements of your operations portfolio.
- Continuously monitor the environment for ensuring FISMA, HIPAA and FDA QSR compliance.
- Identify and notify changes that result in deviations from FISMA, HIPAA and FDA QSR compliance requirements.
- Reduce the financial and legal risk of non-compliance.
Want help with managing your compliance requirements?
Manage change tracking and change management for all requirements-based operational assets.
- Identify the compliance status of each IT asset and process.
- Find compliance gaps in your IT assets and procedures.
- Find and mitigate security vulnerabilities.
- Build compliance strategies that adapt to changing standards

Assess threat and vulnerabilities, security risks and their impact.
Find, diagnose and manage security vulnerabilities. Opsfolio provides built-in feeds for vulnerable databases, websites and mailing lists. It also enables prioritized patch application and phased deployments. Use it to provide remediation information for each identified vulnerability.
Record and monitor compliance status of business, vendors and contract users in an organization.
- Track training needs of users in terms of compliance and record the training undergone by the various personnel.
- Monitor, document and audit the compliance status of users.
- Track changing compliance standards and update user training requirements.


Assess and monitor cybersecurity risk of customer IT assets. Our consultants:
- Scan the client environment for IT assets, their connection points and configuration, and compliance requirements.
- Perform information gathering, security assessment, risk analysis and testing.
- Perform security assessments and reduce risks.
- Perform ongoing monitoring (by request).
Find out who is responsible and accountable and who needs to be consulted and informed about your assets.
In addition to keeping a well documented asset inventory, Opsfolio has a RACI matrix tied to each of your assets. This matrix gives you a firsthand information of which roles are participating in the decision making processes concerning each asset. It tells you who should be informed or consulted on assets, and who would be responsible or accountable, so that they can answer questions that you have for them.


Auto reporting of identified threats and vulnerabilities.
Opsfolio’s audit data collector plug-in uses Third Party detectors that automate threat and vulnerability detection. In addition to the detectors, Opsfolio’s agent collects data such as system information, hardware and software information using internal data sources. Threat feeds are used to get details of threats and vulnerabilities, using which analysis is performed. Automated security responses are generated following the analysis.
Our services perform the following:
- Detects security incidents
- Evaluation and assessment of alerts
- Malware detection
- Analysis, correlation and scoring
- Automation of reporting
- Notification
Protect your assets from insider threats
Loss of data due to fraud and data breaches caused by malicious insiders can wreak havoc on your company’s brand value and customer loyalty. If your company’s name turns up in the news for reasons such as data breaches, then the stock prices are going to go down and it is going to turn your good customers away.
Opsfolio continuously watches networks for malicious activity, tracks new devices added to the network, tracks new applications added to the existing devices, watches for updates to your software libraries and components and notifies you of any suspicious activity.
Want to learn how secure your network is?

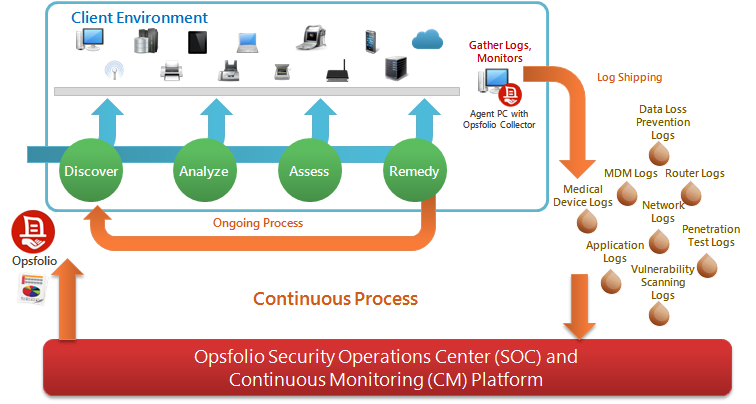
Continuous Monitoring
Opsfolio CM (“continuous monitoring”) is probably the most important part of our suite. Experienced technicians use our security operations center (SOC) to remotely monitor your IT infrastructure. We use the SOC to track changes as well as identify and prevent new risks from occurring. Our personnel and tools continuously monitor ongoing security threats by collecting log data and monitoring changes in your environment.
Tracking Libraries and Dependencies
Is the third-party code in your apps safe to use?
Many developers believe that the open source or custom third-party code they integrate into their code is secure because it’s been used by many others. Just because third-party software passes through many hands doesn’t mean it’s safe. It still must be monitored and checked for security vulnerabilities.
Security flaws in these utilities can affect software that runs on servers, desktop computers, mobile devices, the Internet and hardware appliances—and affect the operations of millions of businesses.
Not knowing where your third-party libraries and open-source code components are isn’t just an information management problem. It can become a security problem
Use Opsfolio to:
- Continuously monitor all your applications and check third-party libraries for vulnerabilities and security updates.
- Perform continuous and periodic checks for security updates and patches for the third party libraries and components used in your application.
- Avoid the cost and effort of manual or DIY vulnerability tracking solutions.
Opsfolio helps you find and reduce the biggest security risks to your code.
Want to find out if your third party apps are safe to use?

Manage software dependencies.
As developers use more and more libraries and components, it’s harder to identify, track and manage them. When dependency issues come up (and they always do), compatibility problems and runtime errors can bring your development work schedule to a halt. Opsfolio provides a structured approach to managing software dependencies.
Use Opsfolio to:
- Provide a centralized repository to store all information about the libraries and components used in your software.
- Keep a record of which versions of the libraries are being used and when they were last updated.
- Virtually eliminate the time and human effort needed to manually track the software dependencies used in your code.
Find every vulnerable component in your application.
 Finding vulnerable components in your app requires a complete list of the latest mailing lists and announcements for every third-party component used in your app. But even if you had this information, would you have the time to search through and use it?
Finding vulnerable components in your app requires a complete list of the latest mailing lists and announcements for every third-party component used in your app. But even if you had this information, would you have the time to search through and use it?
Opsfolio automates the process of finding vulnerable components by:
- Monitoring all the latest publicly available feeds, news and announcements for vulnerabilities and security flaws relevant to your third-party code.
- Notifying you immediately if there is a security flaw or a vulnerability in any of the software components you are using.
Opsfolio security monitoring helps you find vulnerable components quickly and accurately and minimizes the resources you use to find it.
Want to find every vulnerable component in your application. We can help
Remediate
| Potential risks | Opsfolio audits | Opsfolio CM | Benefits/Value |
|---|---|---|---|
|
|
|
|
|
|
||
|
|
||
|
|
|
|
|
|
|
|
|
|
|
Incident Response Handling
Many organizations have a security response plan. But poor design and inconsistent implementation often prevent its being used.
Why is that?
- Plans are often scoped too small. Many security plans and strategies are not designed to respond to organization-wide incidents. Only one or two people know what’s going on.
- Standards and regulations keep changing. You get in compliance, but before you know it, the rules—and your compliance status—change. Some organizations don’t have the resources they need to keep up.
- Many organizations lack specialized knowledge and tools. Planning for and responding to security incidents—and staying legal—requires up-to-date resources.
Netspective tools and services can help you make or update your security incident response plan, quickly and effectively. Effective security incidence response plans must begin long before a breach occurs. Planning is the only way to reduce the number, severity and impact of security incidents. Effective plans help you:
- Prepare your organization by defining responsibilities and roles of the staff, helping you plan resources you’ll need and providing step-by-step guidance when a breach occurs.
- Detect and analyze incidents quickly and efficiently. That includes deciding the scope and root causes of the incident.
- Decide how to notify affected parties. That includes whether the breach requires notification, which entities to notify and whether to make the notification public.
- Contain and remove the breach and recover from the incident. Containment is necessary before any further damage occurs. And, you must remove and replace infected machines.
We offer Netspective™ Opsfolio® Incident Response services as an on-demand, consulting service. We provide a team of veteran security analysts, IT consultants and incident response specialists to help you create or revise your own security incident response plan. Our specialists are familiar with the latest regulations and tools that can help you identify and fix security breaches and minimize the disruption to your organization. Opsfolio Incident Response services provide the knowledge and guidance you need to:
- Use continuous monitoring data to predict security incidents.
- Detect incidents in the client environment with traditional anti-virus and anti-malware tools.
- Notify affected parties as your organization’s standards and government regulations require.
- Track, document, and communicate compromised systems or accounts when they are isolated.
- Specify risk levels for assets, confirm extent of breach and prioritize it by estimating the risk to your organization.
- Identify needed changes to policies or controls such as closing network ports or vulnerabilities and updating signatures and configurations.
- Make changes to IT security systems. Detailed documentation and POAM tracking enable security operations specialists to make needed changes.
- Document the incident thoroughly. Keep records on what led to the breach, identify lessons learned and keep breach-related information as required by your organization.
- Provide ongoing security coverage at all levels of your IT stack
- Customer Support: Our experts are well versed in addressing questions that customers have after a breach has occurred. With the professional knowledge our team possesses, we are able to allay customer fears and provide them with answers and support, when they need it the most.
When you use Opsfolio Incident Response services, you’ll definitely get:
- Less business disruption, measured as faster response time, recovered employee productivity and less damage to your brand.
- Less data loss, enabled by faster discovery, repair and recovery times.
- Faster recovery, enabled by automated incident discovery, analysis and repair processes.
The result: A security incident response process that gets your organization back to work with minimum disruption and maximum resilience.
Clients
Pricing
For custom packages and pricing, please contact sales.
Netspective is a leader in Technology and Consulting services in regulated markets - Healthcare, Government and Medical Technology.
Technology, consulting, and solutions focused on firms impacted by FDA, ONC, NIST or other safety, privacy, and security regulations.




